Networking is hard.
If you have not come from a traditional IT background, the VPC part of the AWS Certification training is tricky. There is talk of CIDR blocks, subnets and spaghetti mess diagrams.
Sort of like the London Underground. Which got me thinking. When I moved to London, the Underground system seemed really overwhelming. But it didn’t take too long to figure out. By the end of my four years, I could tell you which door to get on the train so you could avoid the crowds and get out quickly at the other end.
Turns out there are a lot of similarities between the two. If I could figure out The Tube map with all its zones, stations, platforms and jargon, surely I could figure out VPCs.

Introduction
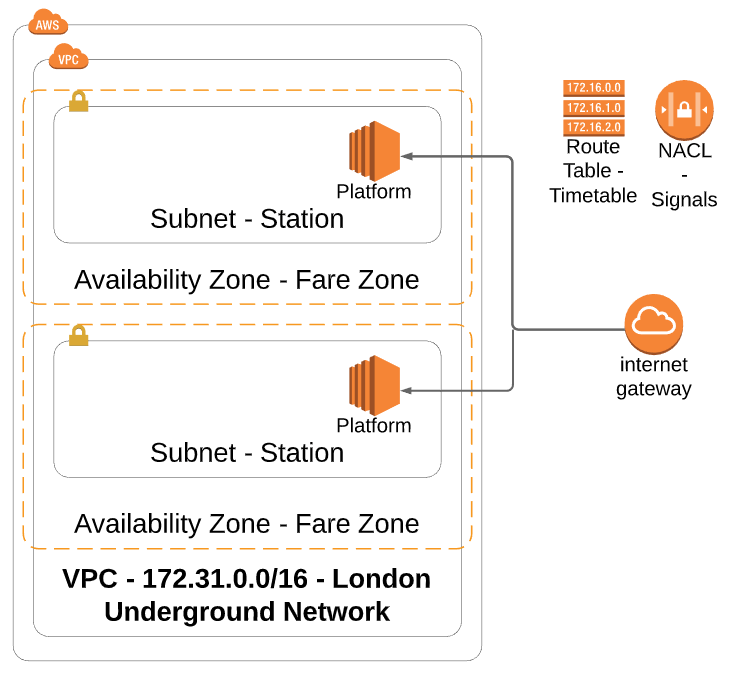
VPC – London Underground Network
Availability Zone – Fare Zone
Subnet – Station
Route Table – Timetable
Network Access Control Lists – Signals
VPC Peering – Travelling on other services
Introduction
Here is the example network diagram from the AWS documentation. This post hopes to break down all the components in this diagram and draw some parallels from the London Underground network.
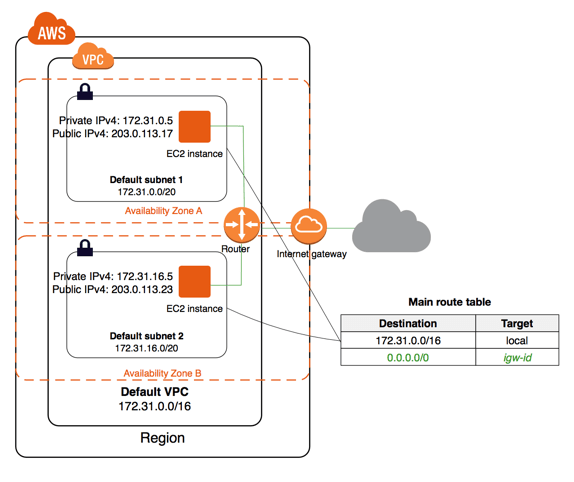
VPC – London Underground network
To put it simply, a VPC is a network within your AWS account that holds your AWS services.
Think of it as your own data centre. You decide how big it needs to be by assigning a range of IP addresses. This is called a CIDR block(Classless Inter-Domain Routing) and it allows us to track and restrict the sort of traffic and users access our instances.
Key things to know:
By default a VPC is isolated from other VPCs unless we ‘peer’ them together.
There is a limit of five VPCs per region but this can be increased.
VPCs span all Availability Zones within a Region.
Availability Zone – Fare Zone
Once you have created a VPC you can start adding Subnets in each Availability Zone.
Think of this like a Station within a Fare Zone. Each Station or Subnet is isolated from the failures of others around it.
Key things to know:
A VPC spans all Availability Zones in a region.
Launching instances in separate Availability Zones protects applications from failing in a single location.
Subnet – Station
A Subnet is like a Station. It can be public or private. Just like on the London Underground network where there are public stations with public access.
There are abandoned stations, staff training stations and mail stations. The kind of private stations the public can’t access on a normal day.
Key things to know:
There can be up to 200 Subnets per VPC. If you would like to increase this you will need to request this through AWS Support.
There are currently 270 stations on the London Underground Network, although they probably didn’t have to submit a ticket to get this increased.
You define which Subnets you want to be exposed to the internet by attaching public IP addresses.
Route Table – Timetable
Each Subnet has a Route Table attached. This creates a set of rules to allow traffic to flow within a set of guidelines.
This means that traffic stays inside the Subnet until a route is created to allow it to travel to the next stop on the network.
Key things to know:
A Route Table tells the traffic which way it needs to go to get to the destination.
The Internet Gateway allows devices on a Public Subnet to connect to the internet.
In contrast a Network Address Translation Gateway (NAT Gateway) facilitates the connection between Private Subnets and the internet.
Similar to how Engineering Stock travel after hours from private stations through public stations.
Network Access Control Lists – Signals
Network Access Control Lists (NACL) allow us to limit traffic to safeguard against mistakes and accidents. Using NACLs, like the signals on the London underground, means we can control traffic flow using a set of rules.
Key things to know:
There are rules for inbound and outbound traffic, so rules must be set up for each direction.
They are stateless, which means that responses to incoming traffic is dependent on outbound traffic. The same way if there is a train in the tunnel ahead, you may be have to wait for it to clear.
You can create a custom NACL but need to add rules as it will deny all traffic by default.
VPC Peering – Travelling on different services
A VPC peering connection allows traffic to be routed between two VPCs as if they were within the same network.
Key things to know:
Transitive peering is not allowed, which means you must have direct access to allow traffic through.
VPCs can be peered with other accounts. The same way you can access National Rail Services from within the London Underground Zones.
This isn’t a perfect analogy but by giving the concepts some context I’m one step closer to getting my head around how a VPC works.
It’s also given me an excuse to revisit all the fun facts of the London Underground which is always good.
How do you put all the components together when explaining VPC concepts to beginners? Are there any other Tube enthusiasts out there in Devland?
Useful links
- What Is Amazon VPC?
- Scenarios and Examples
- Amazon VPC Limits
- VPC Peering
Photo by Valeriia Miller from Pexels

